Red Team Assessment
Test your security against real-world attacks without the risks of negative headlines
Test your security against real-world attacks without the risks of negative headlines

Red Teaming is a comprehensive and realistic approach to evaluating the effectiveness of an organization’s security measures, policies, and response capabilities. It involves simulating adversarial activities to identify vulnerabilities, test defenses, and assess the organization’s ability to detect and respond to sophisticated cyber threats.
Unlike traditional penetration testing, which typically focuses on a specific target or vulnerability, Red Teaming adopts a holistic and adversarial mindset. It mimics the tactics, techniques, and procedures (TTPs) employed by real attackers, combining technical expertise, social engineering, physical security assessments, and other methodologies to uncover weaknesses across people, processes, and technology.
At Redfox Security, we deliver red team engagements to assess an organization’s preparedness for advanced persistent threat (APT) attacks. We do this by emulating real-world attackers’ TTPs used by cybercriminals and malicious insiders. Our red teaming approach includes (but is not limited to) the following:
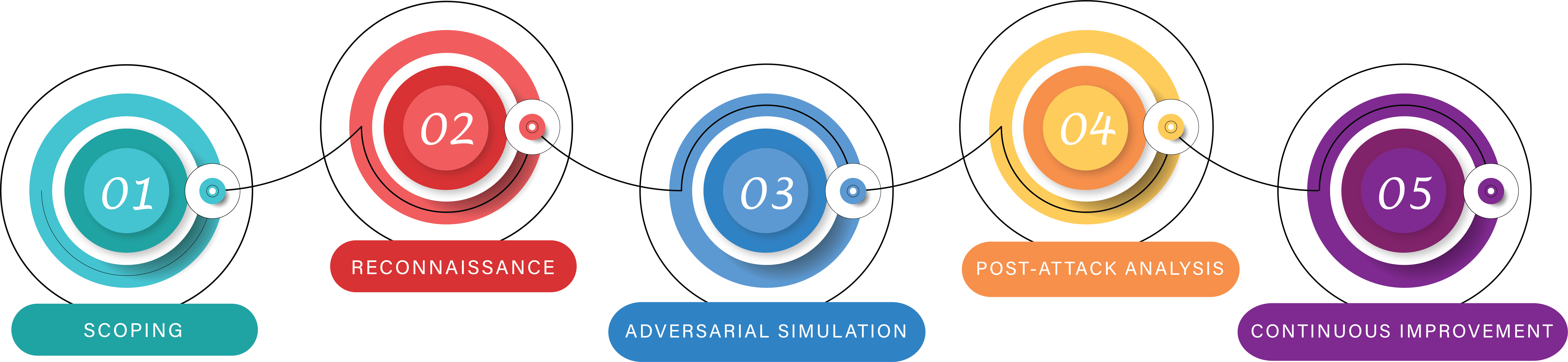
We work closely with you to define the scope of the Red Teaming exercise, taking into account your specific objectives, assets, and threat landscape. This ensures that the simulation accurately reflects your organization’s unique risks and challenges.
Our team conducts extensive reconnaissance to gather information about your organization’s infrastructure, employees, online presence, and potential attack vectors. This intelligence gathering helps us identify potential vulnerabilities and design targeted attack scenarios.
We simulate real-world attack scenarios, combining technical assessments, social engineering, physical security assessments, and other relevant techniques. Our experts employ a range of tactics to identify weaknesses and test the effectiveness of your security controls, from phishing campaigns to attempting physical breaches.
We analyze the outcomes of the Red Teaming exercise, evaluating the effectiveness of your security measures, incident detection and response capabilities, and overall resilience. We provide a detailed report highlighting vulnerabilities, weaknesses, and actionable recommendations for strengthening your security posture.
Red Teaming in cyber security is an iterative process aimed at continuous improvement. We collaborate with you to implement the recommended security enhancements, provide training to enhance employee awareness and conduct regular Red Teaming exercises to ensure ongoing readiness and adaptability.